<%NUMBERING1%>.<%NUMBERING2%>.<%NUMBERING3%> PRTG Manual: Monitoring via SNMP
Monitoring via Simple Network Management Protocol (SNMP) is the most basic method of gathering bandwidth and network usage data.
SNMP can be used to monitor bandwidth usage of routers and switches on a port-by-port basis, as well as device readings such as memory, CPU load, etc. The queried devices must support SNMP.
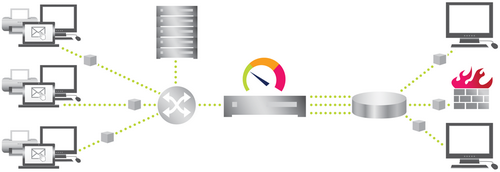
Network Monitoring via SNMP
When this technology is used, PRTG sends small data packets to devices, for example, querying routers, switches, and servers for the traffic counters of each port. These are triggering reply packets from the device. Compared to PRTG's other bandwidth monitoring techologies via flows, packet sniffing, or WMI, the SNMP option creates the least CPU and network load.
Reasons to Choose SNMP Monitoring
SNMP is the most commonly used method mainly because it is easy to set up and requires minimal bandwidth and CPU cycles. If your network devices support SNMP and/or if you want to monitor large networks with several hundred or thousands of sensors, we recommend you start with SNMP. Besides network usage monitoring, another well-known feature of SNMP is the ability to also watch other network parameters such as CPU load, disk usage, temperature, as well monitoring many other readings, depending on the queried device.
In order to use Simple Network Management Protocol (SNMP) for monitoring purposes, it is imperative that UDP packets are allowed to travel from the machine running PRTG to the device you want to monitor and back, which is usually the case in LANs and Intranets. For connections across the internet, to a Demilitarized Zone (DMZ), or for Wide Area Network (WAN) connections, some changes to the traversed firewalls may be necessary. Keep in mind that SNMP V1 and V2c are not secure protocols and should not be used across the internet or insecure data connections. Only SNMP version 3 supports encryption.
To better understand and set up SNMP sensors, you may want to learn more about the principle of Object Identifiers (OID) and Management Information Base (MIB). For more information about this, please refer to the Knowledge Base article in the More section below.
For an overview and details about all SNMP sensors, please see the List of Available Sensor Types section.
PRTG supports three versions of the SNMP protocol: Version 1, version 2c, and version 3.
SNMP Version 1
This is the oldest and most basic version of SNMP.
- Pro: Supported by most SNMP-compatible devices; simple to set up.
- Contra: Limited security as it only uses a simple password (community string) and data is sent in clear text (unencrypted). It should therefore only be used inside LANs behind firewalls, not in WANs; only supports 32-bit counters which is not enough for high-load (gigabits/second) bandwidth monitoring.
SNMP Version 2c
This version adds 64-bit counters.
- Pro: Supports 64-bit counters to monitor bandwidth usage in networks with gigabits/second loads.
- Contra: Limited security (same as with SNMP V1).
SNMP Version 3
This version adds authentication and encryption to SNMP.
- Pro: Offers user accounts and authentication for multiple users and optional data packet encryption, increasing available security; plus all advantages of Version 2c.
- Contra: Difficult to configure. Not suitable for large networks (see below for more information).
It is important to know that if you select an SNMP version which is not supported by the server or device you want to monitor, you will receive an error message. Unfortunately, in most cases, these error messages do not explicitly mention the possibility that you could be using the incorrect SNMP version. These messages provide minimum information only, such as cannot connect or similar. Similar error occur when community strings, usernames, or passwords don't match.
SNMP Overload and Limitations of the SNMP System
SNMP V1 and V2 scale directly with the performance of the hardware and the speed of the network. In our labs we were able to monitor 30,000 SNMP V1 sensors at a 60 second interval with one PRTG server (core and local probe) plus two remote probes with 10,000 sensors each.
However, SNMP V3 has performance limitations due to the SSL encryption. The main limiting factor is CPU power (as well as the other general limits for PRTG). Because of this limitation, you can monitor only a limited number of sensors per second using SNMP V3. Currently, PRTG is able to handle roughly 40 requests per second and computer core, depending on your system. This means that, on a common 1.x GHz computer with two cores, you can run about 5,000 SNMP v3 sensors with a 60 seconds scanning interval; on a system with four cores, you can monitor around 10,000 sensors with 60 seconds interval. The CPU load is at about 50% then. We do not recommend more.
Furthermore, the PRTG core server and probes should run on different computers. If you experience increased values in the Interval Delay SNMP or Open Requests channels of the Probe Health sensor (values above 0 % indicate that the SNMP requests cannot be performed at the desired interval), you need to distribute the load over multiple probes. SNMP V1 and V2 do not have this limitation.
If you run into SNMP overload problems you have three options:
- Increase the monitoring interval of the SNMP V3 sensors.
- Distribute the SNMP V3 sensors over two or more probes.
- Switch to SNMP V1 or V2 if you can go without encryption.
What is the SNMP Community String?
The SNMP Community String is similar to a user ID or password that allows access to a router's or other device's statistics. PRTG Network Monitor sends the community string along with all SNMP requests. If the correct community string is provided, the device responds with the requested information. If the community string is incorrect, the device simply discards the request and does not respond.
Note: SNMP community strings are only used by devices that support SNMP V1 and SNMP V2c protocols. SNMP V3 uses safer username/password authentication, along with an encryption key.
By convention, most SNMP V1/V2c equipment ships with a read-only community string set to the value public. It is standard practice for network managers to change all the community strings to customized values during device setup.
Tools: Paessler MIB Importer and SNMP Tester
Knowledge Base: How do SNMP, MIBs and OIDs work?
Paessler White Papers: Introducing SNMP and Putting SNMP into Practice
German: Paessler White Paper: Einführung in SNMP und SNMP praktisch anwenden
Knowledge Base: My SNMP sensors don't work. What can I do?
Keywords: SNMP,SNMP Technology